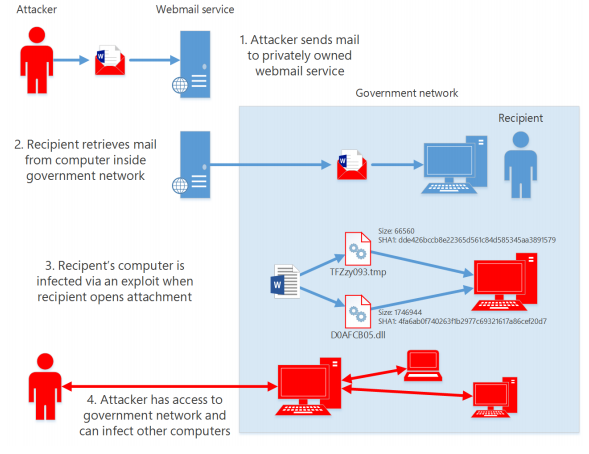
Microsoft published an article about the exploitation of Intel’s AMT tools stealing government data for espionage purposes. The hack works independently of the Operating system which can bypass any windows firewall at the moment.
The malware has been active since at least 2009 primarily responsible for spear phishing attacks on ISPs, government organizations, intelligence agencies, and defense institutes.
The malware is known has been exploiting hot patching feature which allows the installation of updates from Microsoft without system reboot. As per Microsoft Malware protection Center, this is the first time they discovered the exploitation of this vulnerability injecting a backdoor to svchost process which makes it almost invisible.
“As this embedded processor is separate from the primary Intel processor, it can execute even when the main processor is powered off and is, therefore, able to provide out-of-band (OOB) remote administration capabilities such as remote power-cycling and keyboard, video, and mouse control (KVM),” as stated by Microsoft
Highlights mentioned in Microsoft Release as follows :
- Platinum malware focuses on a small number of campaigns per year, which reduces the risk of detection and helps the group stay unnoticed and focused for a longer period of time.
- Platinum malware has focused on targets associated with governments and related organizations in South and Southeast Asia.
- Platinum malware has used multiple unpatched vulnerabilities in zeroday exploits against its victims.
Spear phishing is the group’s main method of infecting targeted users’ computers. - Platinum malware makes a concerted effort to hide their infection tracks, by self-deleting malicious components, or by using server side logic in ‘one shot mode’ where remotely hosted malicious components are only allowed to load once
- Platinum malware often spear phishes its targets at their non-official or private email accounts, to use as a stepping stone into the intended organization’s network
- Platinum malware uses custom-developed malicious tools and has the resources to update these applications often to avoid being detected.
- Platinum malware configures its backdoor malware to restrict its activities to victims’ working hours, in an attempt to disguise post-infection network activity within normal user traffic.
- Platinum malware does not conduct its espionage activity to engage in direct financial gain, but instead uses stolen information for indirect economic advantages.
- In some cases, the combination of these mechanisms—use of undisclosed zero-day exploits,custom malware that is not used elsewhere, PLATINUM’s skill in covering its tracks, and others—has enabled the group to compromise targets for several years without being detected
Details can be available on the paper published from Microsoft