In September, researchers at FireEye Labs discovered a group of malicious adware created by a company based in China and Singapore called NGE Mobi/Xinyinhe. On October 7, FireEye detected a similar adware family capable of completely taking over Android based devices. Researchers have named it kemoge after its CnC domain aps.kemoge.net. It is believed that this attack has its origins in China.
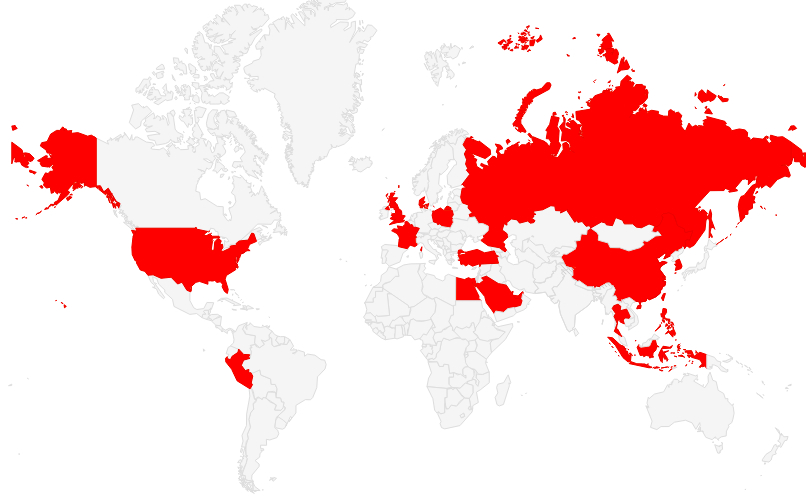
World infection map !
Until now, the malware has attacked victims in over 20 countries that includes China, Russia and the United States. The fact that several of the victims are large scale industries and even government is alarming. The attackers repackage the adware as popular apps which allows them to spread the malware easily.
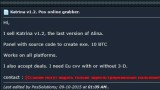
(Adware repackaged as popular apps. Image source: Fireeye.com)
Attack Scenario :
- The repackaged app containing the malicious adware is uploaded by the attackers to third party app stores.
- Users are encouraged to download the apps from the websites where the apps have been uploaded.
- Several aggressive adware that gain the root control of Android devices automatically download and install the apps.
- When these apps are launched, the malware gathers the device’s information and transmits it to the ad server.
- From the background, Kemoge keeps serving ads to the users who keeping seeing them irrespective of the screen activity. Ads are served even on the Android home screen.
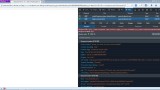
Initially, the malware looks like an innocuous adware to the users but soon it starts threatening the security of the device. In AndroidManifest, the malware registers MyReceiver that launches automatically when the users unlock the screen or the device finds a new network. When MyReceiver launches, it evokes MyService. Both MyReceiver and MyService use the prefix com.google.rp.confirm to disguise them as codes of Google. Few of these samples also use component prefixes such as com.android.ad.sprovider, com.google.ad.sprovider, com.google.system.provider.confirm.
(AndroidManifest code snippet. Image: Fireeye.com)
When MyService launches, it searches for files such as info.mp4, hello.mp4 or bg.mp4 or any other similar file. These are in actuality multi-level encrypted ZIP files disguised as mp4 files. The malware uses password based encryption for protecting the contents of the ZIP file. This ZIP file is further encrypted with DES and the DES key is protected by the second DES key. The second DES key is then disassembled as code bytes. At the runtime, the ZIP files are decrypted in the reverse order by the malware. Second key bytes are assembled into the second DES key which is then used to unlock the first DES key. After the first DES key is decrypted, it unlocks the ZIP file and releases the payload.
After the file is unzipped, following files are extracted:
- apk
- sh
- busybox
- su
- .root
- root_001, root_002, root_003, root_004, root_005, root_006, root_007 and root_008
In total there are eight root exploits executable enabling Kemoge to target a wider range of Android devices. Once it gains root access, the malware implants AndroidRTService.apk in the system partition with the filename Launcher0928.apk which has the filename of a legitimate launcher.
When FireEye tested the malware, it was observed that the app tried to uninstall the antivirus app and other legitimate applications. It is possible that the malware did it to facilitate an attack on the device. FireEye also found one sample of Kemoge on Google Play Store, however its CnC and root exploits were removed. It is possible that CnC and the root exploits were removed from the version uploaded on Google Play Store to pass through its vetting process. However, the malware connects to ads.kemoge.net and adm.kemoge.net for ads.
FireEye has notified Google about the app and has warned users about the possible threats posed by this malware. Users are advised to refrain from clicking suspicious links or downloading apps from unofficial app stores.