Author : Arun Hegde , Security Architect @arun25
Here is a quick summary about my experience at RSA Conference 2014 – San Francisco last month
Highlights of RSA 2014 : Some of the highlights at this year at RSA was cloud security, mobile security ( specially for enterprise), more companies providing SIEM solutions and lot of new companies building security solutions on the public cloud and Big Data. With billions of investments done by huge corporations like Amazon, Google, Microsoft and a lot more, the push will be more on Big Data security in the coming few years. Financial corporations consider cloud as threatening but after speaking to a lot of folks I realized that cloud has invaded the financial sector already. Its just a matter of time before things change as vendors start introducing more cloud based solutions which are regulatory complaint.
1.Future of Appliance based Security : Security solutions have been appliance oriented in the past couple of years, not that it is incorrect. For every security problem, providing appliance based solution has been a one stop enterprise solution. The overhead to maintain these appliances and labor can become very expensive and the current solutions that are available in the market are not helping for scalability point of view. C level executives at various corporations are facing the same challenges and looking for alternatives.
Many vendor companies are planning to change this by integrating multiple platforms & services to a single platform in solving this problem. Private clouds with strong security built in will play significant role in solving this issue. These will be regulatory compliant which of-course is the primary concern of most financial firms.
2. Future of Security : We all talk about modern computing age of inter-connected devices to provide single user experience, but current state of security devices still not there yet (are not inter-connected so far). Firewalls, proxy, mail servers, Anti-spam engine, endpoint protection and many more do not share intelligence with each other thereby act independently to issues. We use data from all such devices and use SIEM products to correlate for appropriate alerting, making it an intelligence provider in most large enterprises. Again the bottleneck of intelligence is as strong as rules are and product limits are. This is the existing state of technology’s weakest implementation point and there is no turnaround for that.
Companies like Symantec are working on this areas to see how integration and intelligence can be unified as a single product. Visionaries are already thinking about such scenarios and working towards it. I found this as a very cool concept and hope to see it in action. Stephen Trilling, VP of Intelligence at Symantec explained something similar in his talk in detail and I have a link to the talk below.
3.Internet of Things Era: Most us have already heard of IoT. The future of the world will be surrounded around IoT and this will create a huge challenge in the Security world. One of Cisco’s executive Padmashree Warrior mentioned “Every company becomes a technology company and every technology company will have security” potentially will change the way we operate things today. The world as we see has been changing rapidly in the world of interconnected devices and this will continue to change with the advancement in processing power. Hence based on these, there will be a tremendous shortage of Security minded professionals.
Interesting metrics from one of the Keynote presenters I noted on the number of connected devices :
- · 5 years back – connected devices 1 billion
- · Current Connected Devices (2014) – 10 billion (which is 1% of the world )
- · Expected connected devices by 2020 – 50 billion connected devices
- · Expected connected devices by 2040 – 77 billion connected devices
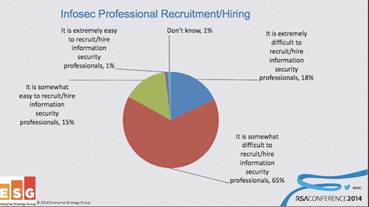
RSA survey on hiring Security Professionals :
Links to various talks and articles on the web :
o Nawaf Bitar,GM – Juniper Networks _ Spoke about some of the ways how existing security has been handled and how it should have been. ( You may find details below )
o Scott Charney, Microsoft – Response to NSA and Some of interesting notes of how information is handled by Microsoft. ( You may find details below )
o Padmasree Warrior & Christopher Young from Cisco : A good talk about IoT ( You may find details below )
o Art Gilliland , HP – Stop Looking for the Silver Bullet: Start Thinking Like a Bad Guy – http://www.rsaconference.com/
o Scott Harrison , Inspiration story about the Charity – WATER. How “WATER is changing the world with a good cause.http://www.rsaconference.com/
o The Next World War Will be Fought in Silicon Valley : https://www.youtube.com/watch?
o KeyNotes at RSA is available here : http://www.rsaconference.com/
o Podcasts : Moving to the SHA-2 hashing algorithm, Protecting data against unwanted surveillance,Two-factor authentication with Duo Security and many more on net-sec RSA coverage http://net-security.org/event/
o Darkreading on RSA topics : http://www.darkreading.com/