New Vulnerability on Android 4.3 allows attackers bypass VPN, exposes protected data
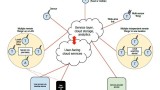
 Security researchers at Ben Gurion University have discovered a serious flaw on Android’s VPN implementation, exposes protected data. As per the researchers, the Android vulnerability allows a malicious app to bypass virtual private network (VPN) configurations( no root permission required) , and ultimately send unencrypted data to an attacker. “The secure data communications can be captured in […] Continue reading →
Security researchers at Ben Gurion University have discovered a serious flaw on Android’s VPN implementation, exposes protected data. As per the researchers, the Android vulnerability allows a malicious app to bypass virtual private network (VPN) configurations( no root permission required) , and ultimately send unencrypted data to an attacker. “The secure data communications can be captured in […] Continue reading →