SUCEFUL – A new Malware capable of copying data from ATM cards
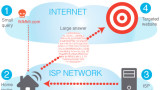
 A new kind of malware named SUCEFUL capable of stealing information from ATM cards and capable of retaining them in the ATM machines has been detected by FireEye Labs. The malware has been uploaded on VirusTotal and the researchers at FireEyes Labs traced it as Backdoor.ATM.Suceful. It seems that the name of the virus is […] Continue reading →
A new kind of malware named SUCEFUL capable of stealing information from ATM cards and capable of retaining them in the ATM machines has been detected by FireEye Labs. The malware has been uploaded on VirusTotal and the researchers at FireEyes Labs traced it as Backdoor.ATM.Suceful. It seems that the name of the virus is […] Continue reading →