 The Lithuanian 000Webhost is one of the most popular free webhosting services and has over 13.5 million users. It ranks among the top search results in Google and is quite popular for its services. However, according to a report from Forbes, the login credentials of these users, that includes their usernames, passwords, email addresses, last names and IP addresses have been leaked online.
The Lithuanian 000Webhost is one of the most popular free webhosting services and has over 13.5 million users. It ranks among the top search results in Google and is quite popular for its services. However, according to a report from Forbes, the login credentials of these users, that includes their usernames, passwords, email addresses, last names and IP addresses have been leaked online.
Thomas Fox-Brewster of Forbes was informed by Tory Hunt, a Microsoft MVP and the owner of a website haveibeenpwned.com. The website displays lists of email accounts that are part of major security breaches. Hunt informed Fox-Brewster that an anonymous person contacted him and gave him access to a database that contains the login credentials including usernames and passwords of the 13.5 million users of 000Webhost. Hunt says that this data is legitimate and has never been leaked earlier. He even found that the passwords were store in a plain text.
When Fox-Brewster and Hunt analyzed the ids and passwords by trying to use them to sign up for the services of 000Webhost, they were displayed a message that the ids are already in use. It indicated that the leak might be genuine. The duo then contacted five users of the free web hosting service who confirmed that the login credentials belonged to them. Hunt even discovered an id in his name which means that someone used it register for an account. The web service does not verify the genuine of the users and allows anyone to register. Hunt subsequently changed the password of the account.
Forbes repeatedly tried to contact 000webhost regarding the breach but did not get any response. Fox-Brewster even tried to call the company on its Lithuanian number, but it did not yield any positive results. Despite his repeated attempt to get in touch with a responsible representative of the webhosting service, he could not communicate with them.
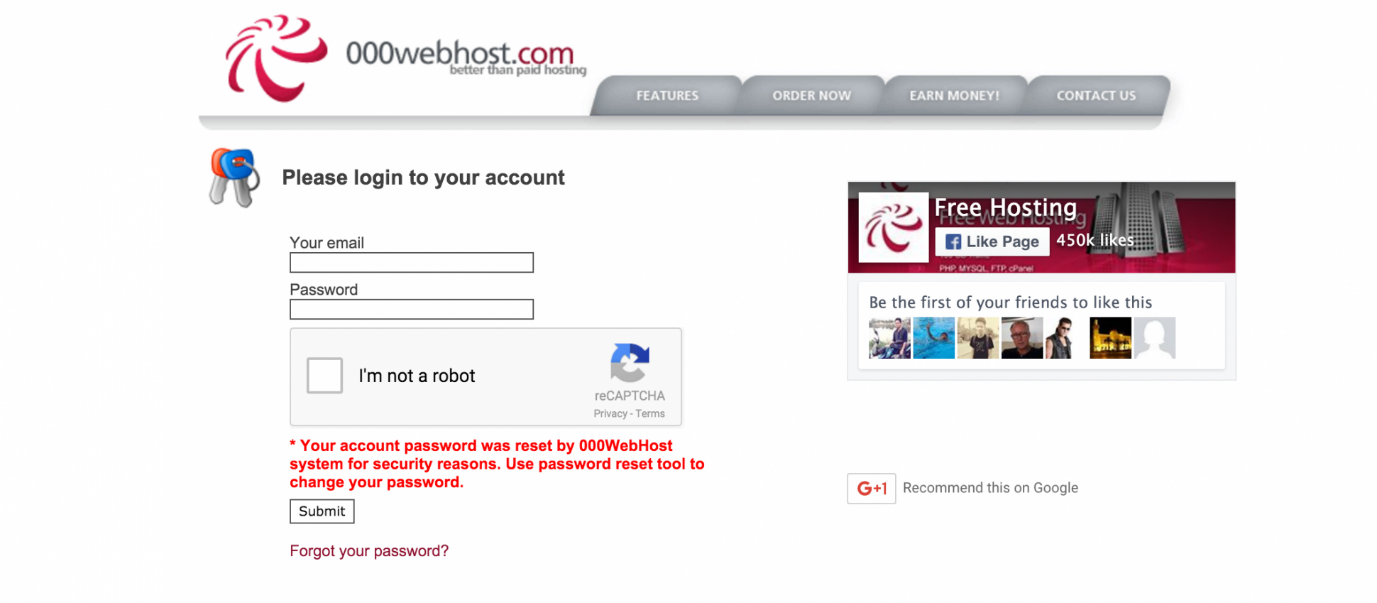
However, on 29th October, Hunt discovered that the passwords for all the accounts have been reset. It seems plausible that the company was aware of the breach and decided to reset the passwords of every single user. The users were displayed a message that their passwords were reset for “security reasons”.
On its Facebook page, the company posted:
“We have witnessed a database breach on our main server. A hacker used an exploit in old PHP version to upload some files, gaining access to our systems. Although the whole database has been compromised, we are mostly concerned about the leaked client information.”
Unconvinced with the approach of the company, Hunt wrote:
“By now there’s no remaining doubt that the breach is legitimate and that impacted users will have to know.”
He further added:
“I’d prefer that 000webhost be the ones to notify [its customer] though.”
Although Fox-Brewster and Hunt repeatedly tried to notify the company, they were repeatedly ignored. The company then reset passwords of all the 13.5 million users. The company should have recognized the breach when pointed out by Forbes and Tory Hunt and should have immediately notified each of its users.
000Webhost issued a statement:
“We removed all illegally uploaded pages as soon as we became aware of the [data] breach. Next, we changed all the passwords and increased their encryption to avoid such mishaps in the future.”
It is the second incident in the last few days when a company that stores millions of users’ data has been found complacent and reactionary in its behavior. A few days earlier, TalkTalk, one of the UK’s leading broadband and phone service provider had its security breached resulting in a leak of credentials of around 4 million subscribers.
With the increase in cybercrimes, companies can no longer afford to ignore the security of the data stored with it. It not only affects the users but also tarnishes the reputation of such company along with financial losses. TalkTalk’s share prices fell significantly after the incident of the leak was reported.
