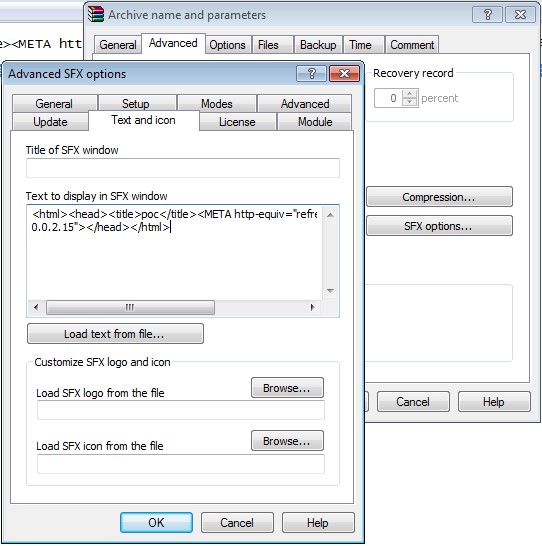
On 28th September 2015, a vulnerability was detected in WinRAR SFX v5.21. It is the latest version of WinRAR, a commonly used file compression tool. Attackers can exploit the vulnerability and compromise a computer with WinRAR installed on it. The bug is in the “text and icon function” under the module “Text to display in SFX window”. The issue was detected by Mohammad Reza Espargham, a researcher with Vulnerability Lab. Espargham also published a proof of concept explaining how the bug acts as a medium for exploiting the target system.
Vulnerability Lab stated that “Remote attackers are able to generate own compressed archives with malicious payloads to execute system specific codes for compromise.” The exploit involves booby-trapping a file that can be easily delivered to a victim through email or any other mode. Once the malicious payloads, it compromises the system which is then vulnerable to attacks.
The bug is detected only in the latest version of WinRAR as there is no evidence of any report of the bug by any of the beta version testers. Beta version of this version of WinRAR was available since February this year.
Pieter Arntz of Malwarebytes has also confirmed the PoC. According to him, the vulnerability is still unpatched. The vulnerability is yet to receive a CVE ID. The modus operandi used by the bug involves compromising the HTML codes displayed in a text window which is displayed while creating an SXF achieve. Once a user opens the SXF archive, the malicious code executes.
(Image: malwarebytes.org)
“The issue is located in the ‘Text and Icon’ function of the ‘Text to display in SFX window’ module,” Vulnerability Lab explained in a post on the Full Disclosure mailing list. “Remote attackers are able to generate own compressed archives with malicious payloads to execute system specific codes for compromise.”