Webroot, warns users about the possible phishing attack for Amazon kindle users. As per webroot, Cyber criminals are attempting to phish Kindle owners into thinking that they have received a receipt from an E-book purchase from Amazon.com.
In real, when a users click on any of the links found in the malicious emails, they are automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
In real we don’t think any of Amaozn’s servers are compromised but this will trick a lot of users give their information to the wrong hands.
The malicious server
Malicious domain name reconnaissance:
starsoftgroup.net – 175.121.229.209; 198.144.191.50 – Email: [email protected]
Name Server: NS1.HTTP-PAGE.NET
Name Server: NS2.HTTP-PAGE.NET
Upon execution, the sample also phones back to the following C&C servers: ( all servers below are malacious)
hxxp://195.191.22.90:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://37.122.209.102:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://217.65.100.41:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
hxxp://173.201.177.77/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://210.56.23.100/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://213.214.74.5/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
hxxp://180.235.150.72/J9/vp//EGa+AAAAAA/2MB9vCAAAA/
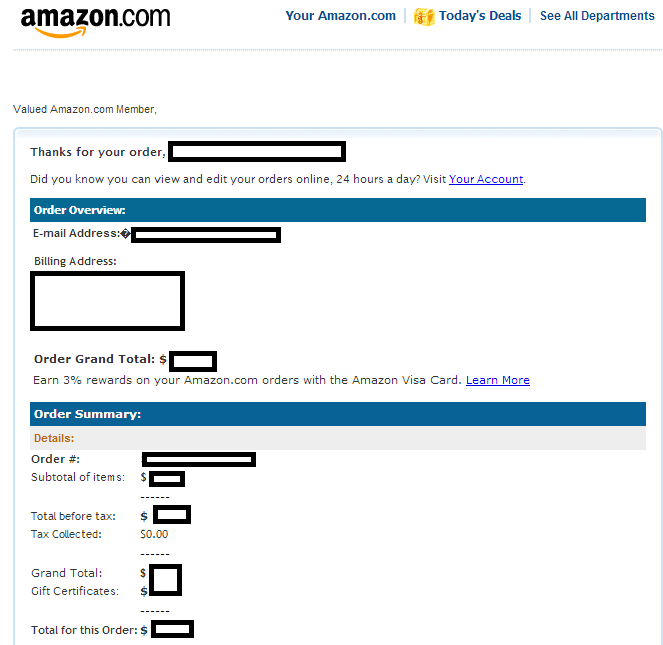
Screenshot of Amazon phish page. Image from Webroot
Article here
