A new variant of the Marcher Android malware is disguising as an update for Adobe Flash Player to steal users’ financial credentials such as online banking and credit card details, according to Zscaler Threatlabz.
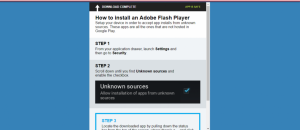
Previously known to baiting users by exploiting pornographic websites and popular games to deliver payload, the malicious Marcher now resorts to posing as an update for the famous Adobe Flash Player. Once a dropper URL is opened, the user receives a message that says that the device’s Flash Player is out of date. Should the user choose to install the update, “Adobe_Flash_2016.apk” will be dropped on their device. If the malware fails to install due to the default setting on Android that prevents installation of apps from unknown resources, the malware gladly provides the user with a step-by-step guide to change the setting.
Immediately after installation, the malware removes its icon from the menu effectively hiding itself from user and register the infected device to its command and control C&C server. It will then send information containing device’s metadata and a list of all installed apps to the said server.
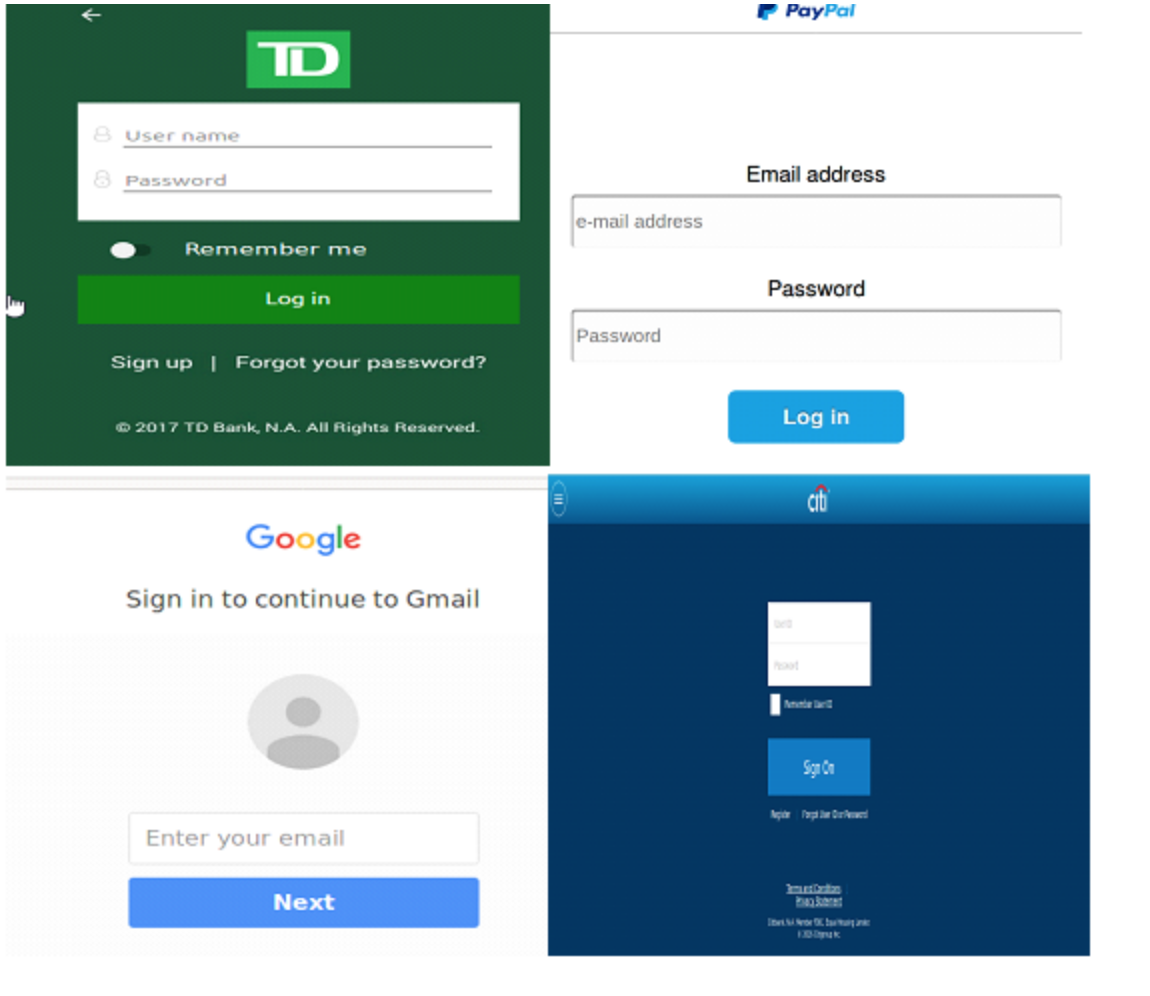
As soon as the user opens one of the targeted apps, the malware overlays a fraudulent login UI that requests banking credentials; an oblivious user will happily provide those credentials and soon the cybercriminals will have the banking details they are after. Such attack does not require the infected device to be rooted nor needs any alerting permissions; the only required permission is android.permission.INTERNET to update the overlay pages and upload phished data.
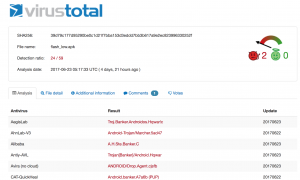
The Marcher variants are often described as sophisticated, however this one is unusually so that it was detected by less than 20 percent of AV scanners according to VirusTotal. This strikingly low detection rate is due to the malware’s obfuscation.
VT detection ( 11/59 (at the time of analysis))
The fake UI is identical to the anticipated screen and hard to distinguish even for experts. Those fake bank login UIs are hosted remotely and can be dynamically updated allowing for more adaptability for this malware attack. Whenever the user tries to lunch a targeted app on the infected device, the request is intercepted by the Trojan and a fake login UI is displayed. Zscaler reported that this Marcher malware is capable of targeting over 40 financial apps so far.
Overlays for phishing Google Play, Facebook and ING-DiBa
According to Zscaler, the best precautionary measure to prevent infections with this malware is to download your apps only from trusted sources like Google Play. Even if you receive warning messages that a software is out of date, refer to trusted app stores for official updates and newer versions. To stop any accidental installation of untrusted apps, keep the “Unknown Sources” security setting of your device unchecked; this setting protects your Android device from threats and keeps most malware at bay.