Gatekeeper is the security feature of Mac OS X that protects users from malicious applications and code execution on their Mac computers. It warns Mac users from installing unsigned apps or the ones downloaded through an unencrypted connection. Gatekeeper does an efficient job of preventing the installation of Trojans and applications with malicious codes. However, Patrick Wardle, director of Synack a security firm has identified a method capable of completely circumventing Gatekeeper and installing malware on the target machine. Wardle has developed a proof of concept to demonstrate the functioning of the method.
(Image Source: arstechnica.com)
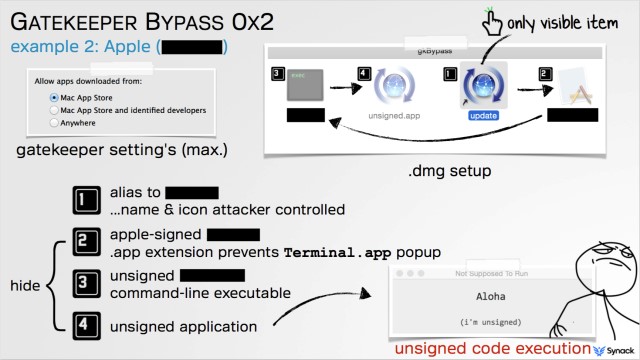
This Mac’s security function checks the digital certification of a downloaded application, and if it is signed by a developer recognized by Apple or downloaded from Apple’s App Store, Gatekeeper lets it through. Once these criteria are met, Gatekeeper exists, and the app can be executed. It does not check whether the authorized app it let through executes another file that results in a malicious behavior. The PoC developed by Wardle explains this vulnerability in Gatekeeper.
Attack Scenario:
The attacker identifies an Apple trusted binary file.
The binary file is packaged inside of an Apple DMG (disk image).
The attacker then manages to place it on the target system.
Since it is a trusted file, Gatekeeper allows its execution.
The Apple trusted binary file then executes another file with the malicious code.
The second file does not any Apple certification to execute and can install malicious codes on the target machine.
According to Wardle, there is an alternate method that allows bypassing Gatekeeper. An attacker can booby-trap malicious plugins into an app installer. The installer will be programmed to open the plugins automatically. Gatekeeper will check the app installer for the digital certification and ignore the plugins. But an attack like it is impractical, and attackers would prefer the first method.
The detected vulnerability in Gatekeeper is alarming since Apple has stated since the introduction of Gatekeeper in 2012 that it is a highly efficient security tool for OS X. A simple technique as demonstrated by Wardle is capable of easily bypassing Gatekeeper. Wardle tested the vulnerability in OS X Yosemite, but the upcoming El Captain could be equally vulnerable. The vulnerability can be easily exploited more sophisticated attackers and hackers backed by larger organizations and countries to target and manipulate computers with sensitive information on them.
The vulnerability is not in the way Gateway operates but is rather in its design. Wardle informed Apple 60 days ago and believes that the company is already working on a remedy. However, it will require more than a simple patch to eliminate the attack possibility. Wardle has suggested few options that can bridge this security gap. These include performing a runtime check libraries load or apps execute to check for any unauthorized file. Another method is to check the dynamic library that is downloaded from the internet.