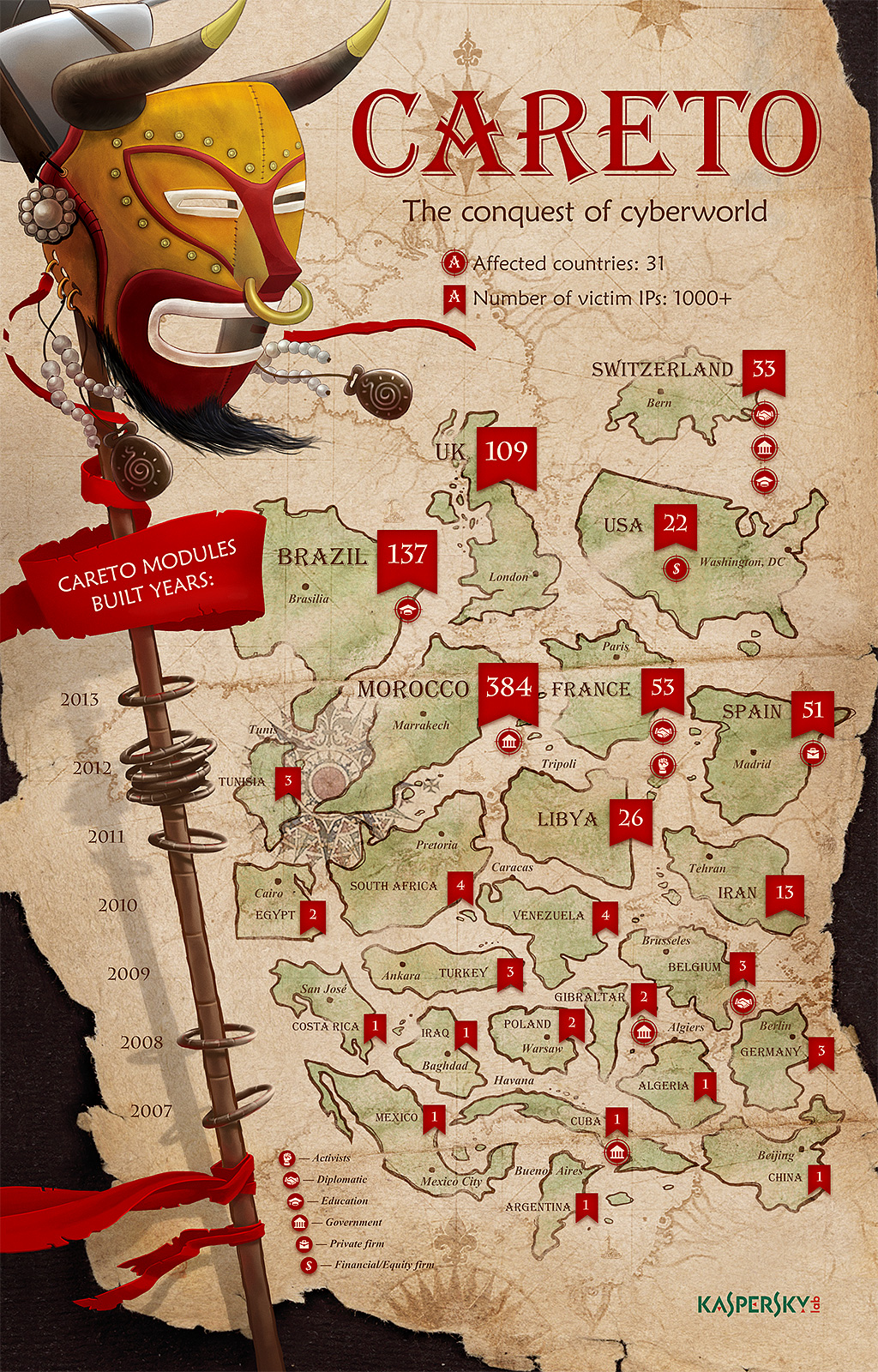
Its almost sounded unbelievable when Kaspersky research published a cyber espionage APT campaign MASK (Careto) that’s been running in the wild since 2007, undetected, targeting 31 countries. The complexity of the tools used for MAST by the attackers are very sophisticated which makes its very special. This includes an extremely sophisticated piece of malware, a rootkit, a bootkit for Windows, Mac OS X and Linux versions and possibly versions for Android and iPad/iPhone (iOS).
The targets of Careto includes Government institutions, Diplomatic offices and embassies, Energy, oil and gas companies, Research institutions, Private equity firms and Activists.
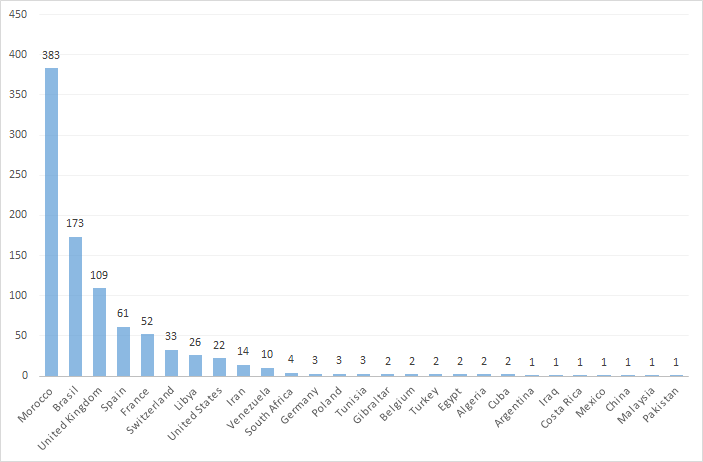
Kaspersky observed more than 1000 IP’s infected in 31 countries. Although the exact number is not known.
The countries that infections were observed were Algeria, Argentina, Belgium, Bolivia, Brazil, China, Colombia, Costa Rica, Cuba, Egypt, France, Germany, Gibraltar, Guatemala, Iran, Iraq, Libya, Malaysia, Mexico, Morocco, Norway, Pakistan, Poland, South Africa, Spain, Switzerland, Tunisia, Turkey, United Kingdom, United States and Venezuela.
How does Careto work ?
The malware intercepts all the communication channels and collects the most vital information from the infected system. Detection is extremely difficult because of stealth rootkit capabilities. In addition to built-in functionalities, the operators of Careto can upload additional modules which can perform any malicious task. Given the nature of the known victims, the impact is potentially very high.
Propagation :
Careto is spread by spear-phishing e-mails with links to a malicious websites. The exploits on the malacious websites are designed to infect the clean visitor, depending on his computer configuration( Windows, Mac or browser specific). Once the user is infected , the malicious website redirects the user to genuine site which may be google or any news portal.
Attack Vectors : There has been multiple vectors responsible for the attack. Howver Adobe exploit for flash players has been dominant. (CVE-2012-0773)
CVE-2012-0773 was the first exploit to break the Chrome sandbox and was used to win the CanSecWest Pwn2Own contest in 2012. The exploit caused a bit of a controversy because the VUPEN team refused to reveal how they escaped the sandbox, claiming they were planning to sell the exploit to their customers. It is possible that the Careto threat actor purchased this exploit from VUPEN.(See story by Ryan Naraine) – Kaspersky
Post Infection :
Upon infection, the malware collects a large list of documents from the infected computer, includs encryption keys, VPN configurations, SSH keys and RDP data. Multiple unknown extensions being monitored that we have not been able to identify and could be related to custom military/government-level encryption tools.
The full list of files that was analysed were:
*.AKF,*.ASC,*.AXX,*.CFD,*.CFE,*.CRT,*.DOC,*.DOCX,*.EML,*.ENC,*.GMG,*.GPG,*.HSE,*.KEY,
*.M15,*.M2F,*.M2O,*.M2R,*.MLS,*.OCFS,*.OCU,*.ODS,*.ODT,*.OVPN,*.P7C,*.P7M,*.P7Z,*.PAB,*.PDF,
*.PGP,*.PKR,*.PPK,*.PSW,*.PXL,*.RDP,*.RTF,*.SDC,*.SDW,*.SKR,*.SSH,*.SXC,*.SXW,*.VSD,
*.WAB,*.WPD,*.WPS,*.WRD,*.XLS,*.XLSX
A paper was published and is available here
Info-graphic :