Two new malwares that affect point of sale (PoS) machines have been detected by the researchers at Trend Micro. The malware have been affecting small and medium sized businesses or SMBs, primarily in the United States.
These two malwares have been named Katrina and CenterPoS by their developers. Trend Micro researchers had earlier reported PoS malwares earlier this year. These were FighterPoS in April, MalumPoS in June and GamaPoS in May. Since then there has been a marked decline in the PoS malware activity. However, this month’s discovery of the two new PoS malwares is an indication that the threats to the PoS systems persist.
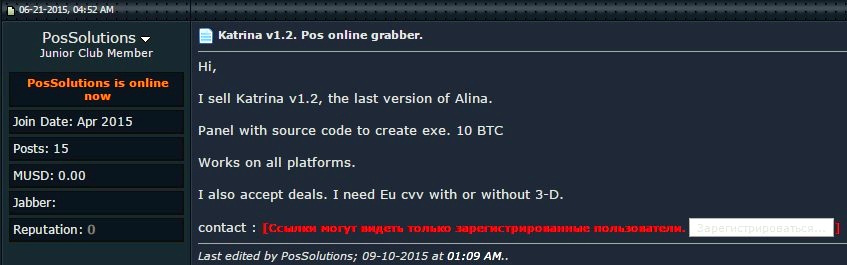
Katrina:
Katrina was discovered for the first time in June this year in underground forums. It is being publicized as the newest version of ALINA, a very popular PoS malware. A close analysis has revealed that Katrina is just an upgrade of ALINA. Katrina has no additional functions as compared to ALINA and there are few minor changes to skipped processes and User Agent.
Katrina operators use two panels to control their malware bot. Until now just two Katrina panels have been detected. The Katrina malware detected is BKDR_ALINA.POSKAT.
SHA1 of the two malwares are:
- f6f1fb61761b24a882af40547aabcb2cd1923f91
- 1a07b2dbb5252a1463e794a59f1763e91c4ab87b
An update command was issued by Katrina C&C for installing NewPoSThing Malware that is downloaded from a specific IP address. Trend Micro wrote about this malware in April 2015.
Image source : Trendmicro
CentralPoS:
Trend Micro discovered CentralPoS in an IP that also hosts Katrina. There is a batch file X.bat, or BAT_XPTDL.A that is also uploaded on the same location which downloads a CenterPoint.exe that is detected as BKDR_CENTERPOS.A from: hxxps://www.dropbox.com/s/{BLOCKED}4isxow5h9ei/CenterPoint.exe.
The attempt of the batch file is to identify InstallUtil.exe in the below mentioned directories and then installs CnterPoint.exe in the very first directory it is able to access.
The directories are:
- C:\Windows\Microsoft.NET\Framework\v2.0.50727\
- C:\Windows\Microsoft.NET\Framework\v3.0\
- C:\Windows\Microsoft.NET\Framework\v3.5\
- C:\Windows\Microsoft.NET\Framework\v4.0.30319\
The malware makes use of a special and constant UserAgent which makes it easy for it to be detected from within the network traffic. Prima facie, CenterPos seems more similar to GamaPoS as both of them are written using Microsoft.Net and do not have Luhn inspection. But, a closer look at it revealed that it is very similar to ALINA.
Below commands are accepted by CenterPoS:
- [/200/], [/401/] = uninstall itself
- [i] [/i], [k] [/k] = stop C&C communication
Below are the components of the stolen information that is sent to the malware’s C&C server:
- OS Version
- Computer name
- Malware version: 1.7
- Local host name
- Victim GUID (MD5 encoded sting combination of Processor ID, Mac Address, Serial number)
- Card track data
- List of scanned processes
The server address is:
hxxp://jackkk.com/2kj1h43.php
The hosted files include two versions of ALINA – Joker and Spark, NewPoSThings’ two versions – 32 bit and 64 bit, BlackPoS, Katrina and CenterPoS and a legal credit card scrapper called Cardholder Data Discovery. The corresponding is like a toolbox for cybercriminals where they can access and upload malware for their activities.
Attack Scenario:
- Target machine’s security profile is lowered
- NewPoSThings (bat) is installed
- Traces of the infection are removed
The primary target of the attackers are the SMBs with majority of them situated in the US. There have been a total of 87 SMBs who are the victims. 77% of them are in the US, Taiwan has 5% while Australia and Brazil both have 3%.
The first detected attack was on 25th August 2015 which means that this is a very recent activity.
| File | Description |
| 32.exe | POSNEWT (NewPoSThings 32-bit version) |
| 64.exe | POSNEWT (NewPoSThings 64-bit version) |
| 315.exe | Alina (Spark variant) |
| 315c.exe | Alina (Spark variant) |
| dux.exe | BlackPos (Kaptoxa) |
| joker1.exe | Alina (Joker variant) |
| Kill.bat | Terminates process, services, disable registries and delete files related to antivirus products |
| Setup.bat | Executes 32.exe or 64.exe silently and will automatically reboot if required. |
| ClearEventN.bat | Clear log events from Application, Security, Setup and System |
| recon.exe | Cardholder Data Discovery Tool (legitimate file; scans files on server, workstation, storage devices for credit card data). |
| kron.exe | Backdoor |
| CenterPoint.exe | A new POS Malware we’ll be calling CenterPoS, detected as BKDR_CENTERPOS.A |
| X.bat | Batch file that downloads CenterPoint.exe. Detected as BAT_XPTDL.A |