With the technology shift from desktop to mobile, more information is sent online for convenience to access to personal information. We trade stocks, banking, pay bills, shop and various things online. With this kind of advancement, risk of exposing information to the bad guys are very high even with the right security practices are implemented. Client side attacks are almost impossible to fight with the existing security systems.
Symantec released quarterly report which describes some of the key ways how hackers targeted financial sectors.
” 95 percent of cases, financial sector institutions were targeted ” – Symantec
Some of the key points from Symantec report :
• The top 15 targeted financial institutions were targeted by more than 50 percent of the Trojans
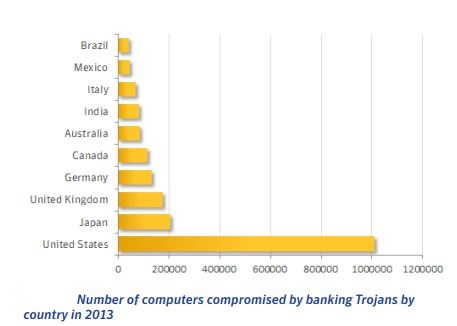
• The most targeted bank is in the US and was attacked by 71.5 percent of all analyzed Trojans
• Two dominant attack strategies are identified: “focused attack” and “broader strokes”
• Institutions in 88 countries have been targeted
• Continued expansion into the Middle East, Africa and Asia
• New institution types are being targeted outside of traditional online banking
• Existing techniques are being streamlined for automation and precision
Attackers have also targeted new emerging cryptocurrencies, the most prominent of which is Bitcoin” – Symantec
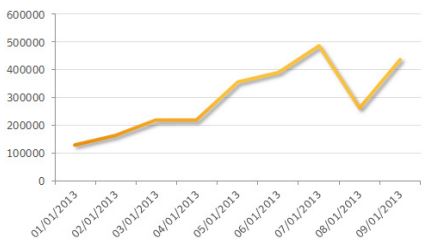
Modern banking Trojans have advanced capabilities for committing online bank fraud and how attackers are well aware of the security precautions behind online banking websites. In November 2013, Symantec analyzed the Gameover P2P botnet distribution in more detail. By enumerating the peer list, we were able to identify computers infected with Gameover. The complete botnet is believed to be made up of hundreds of thousands of active bots.”
Source of above graph and information from Symantec
“