Multiple users have reported to have lost their classic ether approx. $300,000 on reddit on June 29th and June 30th.
An unknown hacker convinced 1&1 staff using social engineering techniques and got hold of https://www.myetherwallet.com/ and tricked the users sending money to the hacker wallet.
The hacker tricked the users and redirected the main domain after hijacking to his own server thereby altering the transactions. He obtained the secret key for anyone who tried to perform transactions and transferred the money to his wallet. The details of the hack is not known however the domain compromise was discovered when the developers of ether classic crypto currency requested users not perform any transactions on twitter.
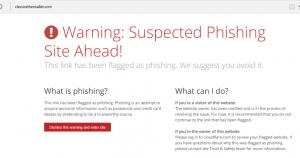
After the initial hack, there was no way for the authors gain hold of their domain. Hence they reached out to cloud flare to mark this domain as suspicious as reported on bleepingcomputer. ( screenshot below)
 After the domain was obtained the domain was taken offline for almost 3 days and informed the users not to panic as long their have the secret keys. They also informed users not to perform any kind of transactions nor post the secret key anywhere online.
After the domain was obtained the domain was taken offline for almost 3 days and informed the users not to panic as long their have the secret keys. They also informed users not to perform any kind of transactions nor post the secret key anywhere online.
The ultimate losses will be faced by its users who lost their Ether however the liability still falls on 1&1 domain company who allowed this to happen without proper verification.